How the Decentralized Web Will Rewrite the Rules of Security and Save the Net from the Barbarian…
The creators of the Internet wanted to build a garden of Eden. They imagined a paradise of openness and freedom. Driven by the spirit of…
The creators of the Internet wanted to build a garden of Eden. They imagined a paradise of openness and freedom. Driven by the spirit of sharing, they saw happy university researchers collaborating across the world with ease.
But they never saw the snake slithering through the trees.
More than anything, the founding fathers of the Net failed to understand the darkness at the heart of the humanity.
Never in their wildest dreams did they see the rise of massive attacks, identity theft, daily data breaches or nation state backed info warriors fomenting discord across the free world. They completely missed malware, spam, DDoS attacks, and ransomware. They couldn’t see that three or four media companies would come to dominate the net, strangling the life from it as they agitated for PIPA, SOPA and now finally the death of net neutrality as orchestrated by their plutocratic sycophants in the FCC.
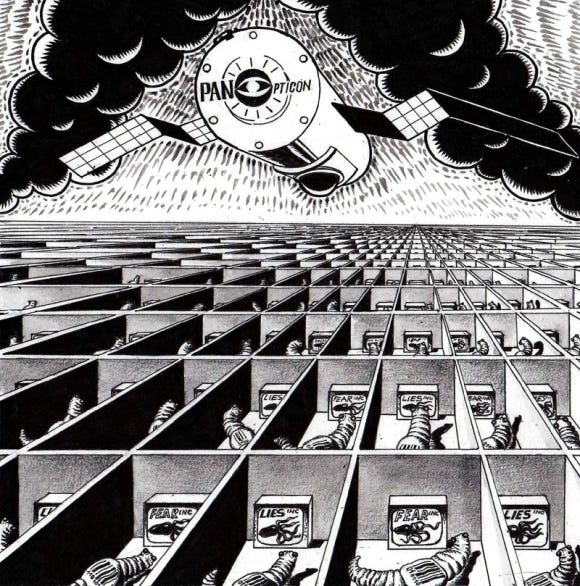
And worst of all they didn’t see the rise of the surveillance state.
They wanted to build paradise but they built a Panopticon to enslave us all.
Now it’s up to us to build a new decentralized Internet and take back our future. That’s the goal of the Cicada project and the Fermat DAO’s Internet of People. In the words of the great Tim Berners-Lee we’re going to “re-decentralize the web.”
We’ll graft it right on top of today’s net and use the old system as nothing but a dumb layer to shuttle packets. That’s all it’s good for now. The old net is rotten right down to the roots. There’s no way to retrofit privacy, security and freedom onto it. We have to build something new.
But to do that, we’ve got to think differently. We can’t afford be naive about the darker angels of our nature.
At Cicada/Fermat we’re under no illusions. We see the snakes in the garden. The same hand that made the tiger made the rose and both will always be there.
The fathers of the Internet sang a song of innocence, blissfully ignorant of the world to come. But now our song must be one of experience.
So how do we build the next-gen net?
There’s only one way.
We have to imagine all the ways to destroy it.
The Decentralized Net
To do that we have to understand the nature of the threats. Who are the snakes in the garden?
There are some obvious ones and not so obvious ones. Crackers and malware writers, identity thieves, terrorists, advanced persistent threats and the intelligence organizations that want to track every single second of our lives stand out as the obvious threats. The not so obvious ones are corrupt companies, overreaching/clueless or bought-and-paid for governmental agencies, and a confederacy of liars, sociopaths and psychopaths.
But it goes deeper than that. We have to assume that any actor in the system can become a threat at any time. Just as Bitcoin nodes don’t trust any other node on the network without verifying their actions, we have to do the same. It’s a twist on the old Russian adage: “Doveryai, no proveryai,” aka “Trust but verify.”
At the Cicada and Fermat projects we say:
“Don’t trust and verify.”
The reason is simple:
Trust is a moving target.
A person, organization or company might start off as trustworthy, only to violate that trust later. A man who cheats on his wife after twenty years just burned up all of his trust overnight. Trust is not fixed. It changes with time.
Leopards might not change their spots but people and organizations sure do.
Today we have no way to revoke our trust from the people who violated it. If we grant one company the right to issue SSL certificates, they may become untrustworthy due to predatory management or a decline in their fortunes, which leads to layoffs, which in turn creates security holes in their systems as their sys-admins slack off on the job while looking for another gig to feed their family. That might be just the security lapse hackers need to crack the system wide open, making them no longer a safe bet.
Better to make the issuance of certificates totally decentralized and algorithmic, delivered through a federated trust of competing entities than to endow a single group with that power. Now we can yank trust back from people who cheat us because power does not rest in a single set of hands.
Other examples are easy to find. A sociopath might build up a ton of positive reputation in the network, only to rob everyone blind later. Imagine a psychotic Uber driver carefully cultivating a 5.0 rating, only so he can hunt down women later, stalking them back to their houses. A government founded on openness and freedom might slide into totalitarianism when a cult of personality comes to power, hungry to cement all control into their own hands, as we’ve seen with the brutal regime in Turkey.
India just finished enrolling 99% of their citizens in a centralized database based on their biometrics. That’s over a billion people. They tried to design the system to not keep data on everything their citizens do. It’s one way. Questions come in and answer goes out. They say it won’t collate data about citizen movements but does anyone really believe that?
How long before that system becomes a target for overreaching government security agencies or before simple incompetence jeopardizes the system? How long before they pass a law that mandates collection of as much data as possible? It’s as inevitable as the sun setting in the evening.
It’s too tempting of a target for people in power.
They can’t help themselves. It’s in their nature.
Now imagine that “trusted” Indian central agency slides into authoritarianism, just as the Turkish government did. Can you see the power of their secret police as they track down and kill anyone they perceive as a threat, from journalists to judges and activists? The ID that tracks all their cashless transactions just made it much, much easier.
If you don’t think it’s possible you haven’t read much of the history of the world. “Throughout modern history, anti-liberal governments have been the norm, not the exception.”
A centralized system is always vulnerable to concentrations of power. The Founding Fathers knew this and they created the system of checks and balances to keep it at bay. A corrupt government can pass a law and then it’s just a quick code rewrite and a new field in a database and suddenly everyone is under constant surveillance everywhere.
No person, group or organization can be invested with trust in perpetuity.
Understanding that gets us to the only possible answer for combating today’s evolving threats:
Federated trust.
Everything must become decentralized, from ID to DNS, to SSL certificates to reputation systems and communication.
The Swarm
Blockchains, when done right, are federated trust.
What do I mean by done right?
Traditional organizations have seen the power of blockchains after scoffing at them early on. Projects like Hyperledger promise to deliver private blockchains. Those can certainly be useful in some instances but not all. Nine banks with a shared blockchain to track deposits between them are kind of trustworthy but not completely. They might all compete on the surface but they also share a lot of the same world views. That means they’re likely to collude when its in their best interests, warping the rules to suit their overall goals and agendas.
A truly federated system is where competing entities and ideologies hold the keys to the kingdom. Think of the banks and the depositors in those banks holding the keys. Or take it one step further and imagine regulators, banks and citizens holding those keys.
That’s true federation.
These are people and organizations that don’t see eye to eye at all. They may even despise and loath each other. Good. That means they have a vested interest in maintaining checks and balances in the system instead of thwarting them to give one group dominance over everyone else.
For a blockchain to be truly useful, its power must be totally distributed across entities that will never see the world the same way. That’s not what we have right now. Realistically the only working blockchains today are cryptocurrencies, which gave us something worse than central banks controlling our money and lives. We’ve handed the power over to an unelected group of secretive mining collectives. This can’t stand and won’t deliver the promised freedom that blockchains promise.
Like the founding fathers of the nets, Satoshi never saw all the problems of centralization, lack of transparency and lack of governance his Bitcoin system would create and so we have to see for him.
That’s why Fermat’s Internet of People and the Cicada project take different approaches to make sure that all the mining power does not fall into the hands of a few rich and powerful mining groups. The Internet of People issues mining licenses to miners based on geography, in order to ensure a dramatically decentralized pool of miners where no one group can dominate. They have no 51% problem.
The Cicada project takes it a step further. We envision a biometric based universal decentralized ID system that welds a single miner to a single ID. Nobody can have more than one miner. Miners are randomly drafted into pools to secure the system. A person might be walking along and their phone wakes up for five minutes to secure the network and then goes back to sleep. This is the federation of trust on a planetary level. It means that everyone who participates in the system helps to safeguard the system and further decentralize it.
But our vision goes a lot further than merely fixing the problem of mining centralization that’s rampant in today’s cryptocurrencies.
Because we’re starting from scratch, and grafting a new decentralized net on top of the old one, we can learn from all the mistakes of the past and design security systems that are woven into the very heart of the protocols themselves.
Imagine a “security blockchain” with pointers to a series of approved binaries and source code, as well as a series of updateable intrusion detection and firewall rulesets and malware heuristics. Nodes are required to run only a few revisions behind or they get frozen from the network. If there’s a massive attack on the system a flag can be set that requires all nodes to run the latest and greatest in a set period of time.
An attacker can try to spin up a rogue node, but it won’t matter. He won’t be trusted by default and the second he communicates with a good node, that node will ask for cryptographic proof that the rogue node is running the right binaries and rulesets. If he’s not, an automatic hit to his reputation gets logged on a “network reputation blockchain.” If the rogue node keeps sending malicious packets and attacking the good node, the good node will simply enact a total and complete shutdown of all traffic via its local firewall. It will then automatically vote to the reputation network that the rogue node is a menace to society. If enough nodes keep voting that node down it will get blocked from all communications for an escalating series of time, from five minutes to ten to an hour and longer. Oh and if you think a bunch of rogue nodes can collude, think again. The good nodes have to prove they’re running approved binaries to the network before they can vote.
But even that’s not enough to secure the internet of tomorrow.
Behold the Naked Mole Rat
We’re also working on what we call “universal security protocols.”
Right now, we fight threats in a pretty stupid way. Take virus signatures, for instance. A malware writer launches a virus into the wild and anti-virus companies have to catch it with a honeypot, study it and then write a virus signature. It’s a one off. That means we’re always playing defense. Wait for an attack and then defend. It doesn’t scale.
We do the same thing when we fight disease. Scientists study each cancer in isolation. They work on drugs to fight breast cancer or Leukemia or colon cancer on a one off basis. They brute force through a series of chemical combinations, hoping one of them will make a difference. This is the same approach to fighting disease in the digital world. Wait for attack and fight each attack with a one off solution.
But nature offers us a better template:
The Naked Mole Rat.
The NMR may be one of the ugliest creatures on the planet but its proof that you can’t judge a book by its cover. It’s immune system holds the key to a universal cancer mitigation system.
Why?
Because the NMR can’t get cancer.
You can bombard that son of a bitch with radiation that would kill a man a hundred times over and it’ll shrug it off like a minor headache.
So how does it work? It’s immune system does two things:
If cells cluster together it nukes those cells
If its cells start dividing too fast it nukes those cells
Simple and efficient. All cancers share both of those characteristics. Cancer solved.
We can do the same for digital cancers: Discover their universal characteristics and kill them off.
When I was a sys-admin, I found a simple answer to most virus infestations. In Windows I set the various registry keys that allowed programs to start with Windows to “read-only” for all users. That meant I had to change it when I installed a new program I wanted to start (which was rare) but when a virus infected the machine it couldn’t start. It wasn’t perfect but it saved me from numerous zero-days.
Now, it doesn’t mean that new types of digital cancers will never show up over the horizon with different characteristics but whenever they do, it will share metapatterns we can exploit as well. Understanding metapatterns are the key to building amazing system architectures. Tyler Volk’s book clued me into their existence twenty years ago and now I see them everywhere.
In the short term, until universal patterns emerge, we can use the old fashioned brute force approach and write a one time signature to the security chain rulesets. But as the new attacks swarm, we’ll study their universal characteristics and cut them off at the source.
We need to design these universal attack mitigation systems right into the very heart of tomorrow’s decentralized Internet. That’s why at Fermat and Cicada we’re working to build the next generation of security protocols into every layer of our stack. To do that we just have to see clearly what the threats are and create heuristics that stop those attacks before they even start.
Is it wildly ambitious and even insane for us to tackle?
Yes.
But we’re doing it anyway. If not us, who? If not now, when?
Besides, we have a lot of data to work from now.
We have years of crafty and insidious assaults on the open foundations of the Internet to study. The snakes have show themselves clearly. And now that they’re out in the open, we can build the NMR’s anti-cancer system into the lowest layers of tomorrow’s TCP/IP and HTTPS.
If we do it right, we can lock in open for a generation to come.
Of course, eventually the snakes will evolve again. But that’s the nature of the world. It’s a pendulum that swings back and forth between good and evil forever and ever.
And when the snakes change their patterns, it will be up to the next generation to seize the day, and recreate the system to stop the threats that we’ll never be able to imagine now. I trust them to do it.
But we have to do it first or they may never get the chance.
So come join Cicada/Fermat. Jump on Fermat Slack (link at the bottom of the page) and talk with the team.
Together we can code the future and save the world.
############################################
If you enjoyed this article, I’d love it if you could hit the little heart to recommend it to others. After that please feel free email the article off to a friend! Thanks much.
###########################################
A bit about me: I’m an author, engineer and serial entrepreneur. During the last two decades, I’ve covered a broad range of tech from Linux to virtualization and containers.
You can check out my latest novel, an epic Chinese sci-fi civil war saga where China throws off the chains of communism and becomes the world’s first direct democracy, running a highly advanced, artificially intelligent decentralized app platform with no leaders.
You can get a FREE copy of my first novel, The Scorpion Game, when you join my Readers Group. Readers have called it “the first serious competition to Neuromancer” and“Detective noir meets Johnny Mnemonic.”
You can also check out the Cicada open source project based on ideas from the book that outlines how to make that tech a reality right now and you can get in on the alpha.
Lastly, you can join my private Facebook group, the Nanopunk Posthuman Assassins, where we discuss all things tech, sci-fi, fantasy and more.
############################################
Thanks for reading!
Hacker Noon is how hackers start their afternoons. We’re a part of the @AMI family. We are now accepting submissions and happy to discuss advertising & sponsorship opportunities.
If you enjoyed this story, we recommend reading our latest tech stories and trending tech stories. Until next time, don’t take the realities of the world for granted!